Week7: Mobile Device Security
According
to this year’s Symantec’s Internet Security THREAT REPORT [1] mobile threats
are increasing in proportion with a number of devices on the market. Market
penetration is expected to reach 4–5 billion by 2017 (about 80% of the global
adult population!) [2][4]. Smartphone and tablet use is growing, mobile OS
vendors are racing and the number of mobile apps is skyrocketing!
Number of mobile devices is estimated
to reach 5 billion in 2017 [4]
It’s
no surprise the success of mobile devices. A smartphone integrates several
tools into one device one and helps people solve a variety of problems.
Unfortunately not all mobile users are aware that there is a price to pay for such
convenience and accessibility.
On
mobile tools people typically store personal information and contacts. These
tools are small but powerful computers with constant access to the internet.
People recognize the need for antivirus software and know to stay away from
unsafe websites on their PCs. But does they apply the same level of concern
when using their phones or tablets …or even their smart TVs?
Research
by McAfee leaves us with no illusion. A number of mobile malicious software
samples are skyrocketing. It’s because information processed through mobile devices
is very valuable.
Number of mobile malicious software samples discovered yearly [6]
Threats caused by the software and use of device
vulnerabilities started to become considered a serious issue. High-school
hackers have been replaced by skilled professionals and an ever expanding
underground market. You can quite easily buy almost anything in there: from credit
and debt cards data to packs of logins details, emails, HTTP, FTP, POP, SMTP
accounts; Windows passwords or even order a targeted attack.
It's
really surprisingly easy to spy on someone’s smartphone or steal their data. For
example, if you’re a suspicious husband/wife you can install a small invisible locater
app on your partner’s phone. If you lack the technical skills you can simply order
a phone with the locater app already pre-installed and give it as a gift. The bonus-gift
for you is access to an online portal that provides access to your partner’s messages,
pictures, phone calls and locations. However, I must advice against this, as like
hacking it’s a crime.
So,
what can YOU do with your phone or tablet to prevent all that?
Let's
start with the basics! You absolutely must have a pass code on your device …and
it shouldn't be "1234”. Recent research and information concerning
security breaches shows that people too often use very simple authorization:
Top 10 passwords stolen recently from
Facebook, Yahoo,
Google, Tweeter, LinkedIn and more [5]
Google, Tweeter, LinkedIn and more [5]
Top
10 iPhone passcodes (includes “1234”, “0000”, “1111”, etc.) [7]
You
should also be very careful when downloading apps from stores other than the
legitimated ones. Google Play may not be as safe as Apple Store but it’s still
much safer than third-parties stores. I would suggest that your best bet is to
use only the authorised stores.
The
apps you download ask for permissions during the installation process. Pay a
lot of attention to that – for example why a simple game requires access to SMS
privileges? Does it really require them? Be very careful with the permissions
granting, especially if they regard SMS! SMS can be used to send costly
messages without your knowledge …or even worse to authorize your bank
transaction. In fact one of the widely used mobile malware does exactly that –
it cooperates with a Windows key-logger and steals transaction codes of your
bank.
Once
you’ve downloaded and installed an app you should u p d a t e both your mobile OS and the apps!
There’s a reason why Windows is updated so often and new patches are being delivered
to most of our PC software. Give a chance also to the mobile developers to
improve your security.
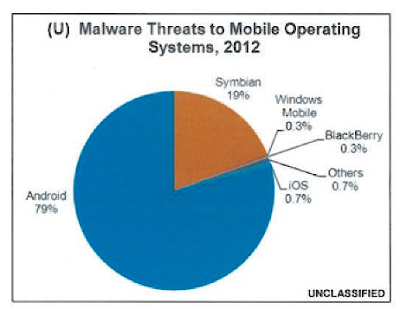
Whereas
Apple iOS based devices are still quite safe (Apple checks each and every
application they sell in the store), owners of mobile devices with Android
should be probably more worried. Due to the statistics the amount of malware
threats designed for Android is 100 times bigger than for the iOS [8].
Thankfully there are a number of good antivirus apps for Android, be sure to
get one of them.
Malware threats for different OS [8]
In
the business world the issue is called BYOD (Bring Your Own Device) and regards
all types of private equipment an employee may bring to the office and connect
to the company’s network. With mobile devices it has become more serious because
it is impossible to prevent your employees from bringing their (smart)phones to
work.
On
the other hand, there are company devices owned by employees. They may be taken
out of the office, but still have access to sensitive company data. What if
they are stolen or lost? Can you imagine a competitor having access to your CRM
with all contract and client information or law-protected “personally
identifiable information” (PPI)… It potentially could lead to serious trouble.
Enterprise
Security policy creators are now trying to solve the issues by creating company
networks, special guidelines and rules and monitoring them. For example, networks
are created for personal devices only. There are special Mobile Device
Management (MDM) systems which allow companies to register, control and track a
device remotely. Corporate “app stores” are also getting more popular as they
contain only apps recognised as safe by an organisation.
But
the overall situation doesn’t look bright. Laws and regulations aren’t
developing as quickly as the technology is evolving. As in a well managed organization each state or union (e.g. the European Union) should have their own Research
& Development department taking care of their citizens security and
privacy. R&D would not only keep up with the latest technology but also provide
guidelines and feedback to policy makers. However, the reality is completely different:
government departments that apply technology effectively use it to spy on
people (NSA is a great example) and organisations like GIODO meant to protect
our data, writes laws that are years behind the technology. I hate to admit
that, but it looks like we’ll have to rely on ourselves for personal data
security.
Approach to personal data security
Some questions for discussion:
1. Do you protect your mobile data? How?
2. Do you have any policies regarding BYOD at work?
If so, are the policies difficult to follow?
If so, are the policies difficult to follow?
3. Have you heard about any interesting
facts from the mobile security area?
Sources:
[1] Symantec’s Internet Security THREAT
REPORT
[2] The Mobile Economy 2013, GSMA and A.T. Kearney report
[3] http://www.webroot.com/blog/2012/09/24/new-e-shop-selling-stolen-credit-cards-data-spotted-in-the-wild/
[4] http://mashable.com/2013/10/03/mobile-phones-2017/
[5] http://niebezpiecznik.pl/post/2-miliony-hasel-wykradzione/
[6] University of London International Programmes; Malicious Software and its Underground Economy: Two Sides to Every Story
[7] http://danielamitay.com/blog/2011/6/13/most-common-iphone-passcodes
[8] DHS-FBI Bulletin: Threats to Mobile Devices Using the Android Operating System
[2] The Mobile Economy 2013, GSMA and A.T. Kearney report
[3] http://www.webroot.com/blog/2012/09/24/new-e-shop-selling-stolen-credit-cards-data-spotted-in-the-wild/
[4] http://mashable.com/2013/10/03/mobile-phones-2017/
[5] http://niebezpiecznik.pl/post/2-miliony-hasel-wykradzione/
[6] University of London International Programmes; Malicious Software and its Underground Economy: Two Sides to Every Story
[7] http://danielamitay.com/blog/2011/6/13/most-common-iphone-passcodes
[8] DHS-FBI Bulletin: Threats to Mobile Devices Using the Android Operating System






Quite interesting article, but in my opinion is not only the problem of mobile phones apps, but all kind of devices. FBI can turn on laptop cameras if they are suspecting someone (http://gizmodo.com/fbi-can-secretly-activate-laptop-cameras-without-the-in-1478371370). Even you can turn it on in case your notebook had been stolen – simple software will do the trick.
ReplyDeleteTo answer your questions – I try not to keep any data on my phone – contacts, messages, some photos – that’s all what I have. As many people I also have on-line bank account, but it’s better to use security token rather than text messages to confirm a transfer. In many bigger corporations you receive one in order to access any data or site. Many websites are also blocked such as Facebook or others to prevent any leakage of information. Not only it helps with security, but increase productivity as well. Employees do not waste time and time is money!! Gladly I do not work in so harsh conditions.
When we are speaking about mobile security area, I would like to warn you about electronic pick pocketing (http://www.youtube.com/watch?v=POIMXohFYSQ or http://www.youtube.com/watch?v=cAwhtYd4tko).
Most new cards use RFID System (Radio-frequency identification) nicely called Pay Pass or Pay Wave , with which, you can be easily robbed basically anywhere. It can be prevented, but if you want to know how… Watch my videos :)
Thanks for your comment, I already heard about pick pocketing, but the movies help me realized how it may work in practice and how common it is... I keep my RFID cards in small metal wallet anyway, so I hope pick pocketing is impossible in may case... But generally speaking people should be more careful when it comes to securing their electronic money. They should pay attention not only to what may happen to their Pay Pass cards but also where they enter their cards credentials.
DeleteI of course agree that the issue regards all device types, but when it comes to mobile devices people lack awareness of threats and way to defend. I was almost sure you guys are aware – you’re most from the IT area. That’s exactly why I wanted to hear about your experience and thoughts on the topic. Many thanks.
The other way are small RFID card holders (RFID Stop, Safe Case etc.), which are very efficient - personally I have those and when my cards are carried in them I cannot use them to pay with PayPass - I have to take the card out from the case.
DeleteKasia, a very interesting article! From now on I will perceive you as an expert in this matter :-) And as the expert I want you to answer me: are our cellular phones more exposed to the attacks from an outside or from an inside? I am interested in it, because there is some information reported about the disturbing actions undertaken by mobile phones' manufacturers and operators, who install an illegal software on our phones, which enables them to collect our private data.
ReplyDeleteHave you heard about Carrier IQ case? In 2011, it was revealed that Carrier IQ - an American mobile operator, created an illegal tracking program, which was later installed on mobile phones (with Android system) sold by CIQ to its clients. This program was so effective that the company acquired a lot of information about their clients’ activities. What is worth mentioning - this application was not visible to users, it was impossible to detect it by somebody who is not whiz-programmer.
You can find a video on the internet (made by a man, who discovered Carrier IQ scandal) showing what happens with a phone with CIQ's tracking application installed:
http://www.youtube.com/watch?v=T17XQI_AYNo
Firstly, CIQ ignored the issue and did not admit the fact that was illegally retrieving and collecting data from users. But later on, their claimed that the company did not use the information possessed and that all the data was encoded and safely stored. Fortunately for mobile phones users, legal institutions did not believe the operator explanations. The European Commission took a closer look to CIQ’s software, to consider whether it was a violation of privacy. There were some legal actions taken against Carrier IQ, AT&T, Sprint, T-Mobile (mobile operators) and APPLE, Samsung, HTC, Motorola (phones manufacturers).
That happened almost 2 years ago, and I wonder if something changed? Maybe there is still a "collecting anonymous data" software in our phones, and we do not even realize it existence. So how we - the users can protect our privacy if we are not aware that our data is stolen?
Thanks Piotr, but I’m not an expert (at least not yet ;). I got interested in the topic last year when we had that as one of the courses on studies, so there’s still a lot for me to learn. I haven’t heard before about Carrier IQ, but I’ll definitely learn more about it. I’m shocked with the movie you posted! That probably answers your question and I need to thank you for asking it. It made me realize one more very important view on mobile security and privacy.
DeleteI’m sure you already know if our phones are more exposed to the attacks from outside or from inside? There’s certainly almost unlimited variety of possibilities for the devices manufacturers to spy on us. With external apps you may decide if you’d like to install them or not.. With an invisible app preinstalled by the phone producer, “hardcoded” into hardware, controlling all your actions on the phone – making any decision is impossible… I have to admit that knowing about all this is makes me feel very uncomfortable…
A little scary, isn’t? And what is more: In 2011, the researchers from the North Carolina State University decided (inspired by the affair described above) to test the most popular brand of mobile phones sold in the U.S. (for example: HTC Legend, HTC Evo 4G, Samsung Epic 4G). Those phones were based on the Android system. The researchers studied 13 main applications of Android system, which were essential for the phone to work properly (i.e.: for sending messages, or enabling the access to the address book).What were the conclusions of this examination? The researches revealed that those applications used private data of the users without asking them for permission to do that. In addition, they sent data to other applications installed on the phone, which had forbidden or limited access to users’ private information. Therefore you can see, that our data can leak out even when we do not use the most complicated applications, but only the basic ones! And we do not even know about it.
DeleteHave you heard about such activities on Apple devices? Looks like we need to switch back e.g. to old Nokia devices if we don't want to be tracked. I can already see scenes like in science fiction or action movies, where secret agents are equipped with old phones, because those are the only ones that aren't tracked ;)
DeleteIn the Carrier IQ case also Apple was prosecuted, so I assume that their devices are not free from the applications which collect data illegally.
DeleteI have always thought that Nokia is creating the coolest mobile phones :) And now, it seems that it may also have other advantages...
Doh I also wanted to write about CIQ :)
DeleteAs far as I remember, it was mixed inside the Android system core and was very hard (or impossible) to turn it off. It was also used in USA to show the road traffic load.. globaly. Furthermore, it recored everything you pressed on you phone, so it is quite easy to think what data it provided to authors and how careful people should be using their smartphones.. because not only them are smart :)
Topic is quite actual nowadays, indeed.
ReplyDeleteBeing quite close to technology I am a bit easy with regards to mobile data security. My take on that is : "I am too small for CIA or NSA to dig on me" :)
On a serious side, I am willing to sacrifice some security for a comfort and features modern mobile phones give me.
In my company we have a "corporate security policies", which basically force to set a long enough password, allows administrator to remotely wipe the phone and so on. It does not help that much, because lots of people just have 123456 as their passcode.
A really interesting study could be found here: http://www.nature.com/srep/2013/130325/srep01376/full/srep01376.html
It describes how unique our mobile traces are.
I think that key to the effective security policy is awareness. Long time ago I also had a passcode like “1234”, but when you tell people that all the other people use it too, and what may happen and a consequence e.g. when they lost a phone, they start to wonder. Not immediately and not all of them, but some will change the passcodes and start think about what do they keep on the phones.
DeleteWith the approach like “I’m to small for NSA” we can soon became part of the world described in Geroge’s Orwel “1984”. I’m aware it’s exaggeration, but we can’t just be Ok with it because it is convenient. We have right to convenience and privacy at the same time. They don’t give you the fancy smartphone in exchange for your private data, you pay for it – you already paid for the service. Why are the so greed?
Good point for passwords, people don't listen to voice of logic before something bad happens to them, but that's everywhere not only in IT security, that's the human nature.
DeleteWith regards to second bit , well here we could argue a bit. When you buying a phone - you pay for a device itself and its abilities (connectivity, camera, gsm, gps ...etc.)
When you're using services on your phone (Google maps, Apple's Passbook, Search ...etc.) are you actually paying for each of them ?
Directly - No. Indirectly - Yes, by providing them your private data for they could sell it to advertisers.
Would you agree to pay for Google Maps, Gmail, Search and so on directly ?
You are of course right, especially with google and facebook - we get them for free in exchange for our data... But take a look at the topic started above by Piotr... That's something scarring!
DeleteIndeed. There is a certain "creep" level about amounts of private data that currently available for corporations.
DeleteNo doubts that we need to know what personal data certain company (service) collects and why. This information should be available publicly to everybody.
p.s. on a "creep" topic:
recently it was another scandal about companies collecting private data, this time LG was involved. They just released new series of smart TVs, new models included built-in camera and pre-installed Skype. What users didn't know is that this camera was also recording and transferring to LG what users were doing while watching TV ... were they watching alone or with somebody ? were they sitting on sofa or laying on bed ? what channels did they watch and so on ....
now , this is creepy isn't it ?
luckily, after all the buzz over the Internet, LG disabled that feature ... but when all will forget about that who will stop LG to turn it on again ?
It is quite common for a trojans/viruses to automaticly turn on the camera and send everything to authors.. be aware of what you are doing in front of the computer and, for more security, stick something onto the camera if you are not using it ;)
DeleteHello
ReplyDeleteI wish to thank you for the useful information you gave us.
In relation to mobile protection, I have been only using pass code on my mobile set although it might be easy to guess. I also set the device that in case someone enters the pass code wrongly, after 5th try, the mobile phone will automatically delete all data I have, such as pics, music and etc.
Our company had not been really secretive about data on PCs. The reason perhaps is they are not really secret. But as far as I know all data related to contracts and financial issues are kept on manager’s PC only and no one has access to them. Oh, one more thing. Basically, all devices have password that every other week the department of informatics changes them.
Many years ago there was an app that first someone was sending a request via Bluetooth to for example transfer a sound, but it was actually malware that could steal all contact numbers. From that moment I kept my eyes open on accepting or downloading anything on my phone. Anyway after reading this subject I made decision to seriously think about improving the security of my mobile phone.
But to be honest... it's sad that as a regular citizen of planet Earth I cannot trust to anyone...
Great article! I own smart phone with Android so according to the information I have just read I should start worrying more than owners of Apple products. Nevertheless I think I have quite good solution. I download not to many application, always from Google Play, I read information about application`s permission, I turn on the Internet access only if I need. I almost don’t use Internet Browser, only emails using special application. I turn on GPS only if I need. You can still say that Google can have some hidden application which can turn on anything in my smart phone without visibly effect but I think we all had to accept some time ago PRISM so I wish them a lot of fun during reading my emails, sms etc.:-) I have not ever had policies regarding BYOD at work. Your article is quite complete so I don’t have anything to add :-)
ReplyDeleteI think you made a really good point. Mobile devices are computers, just smaller, and much more personal. A compromise smartphone is a perfect spying device. They are equipped with a microphone and a camera, they know our current location, the contents of our mail and SMS messages, and our voice conversations. And we always carry them with us. Quite scary.
ReplyDeleteThe BYOD policy in my current work is "no". Plain and simple. Of course we bring our smartphones to work, but we never connect them to the company network. The main disadvantage is it's harder for us to test our products (mostly web applications) on a big range of devices. If we could connect our own devices we would be able to test our products on them. But I fully understand the security implications.
As a side node - the organisation I work for, organises a yearly security (including mobile security) conference in Warsaw. If you are interested in security, you should really consider going.
And since I recommend podstasts this week - there is a great podcast all about security, called "Security Now". It's quite technical, but I highly recommend it.
Thank you for this article! I know we should be careful with all the datat we store - not matter on which kind of device. But you gave me an opportunity to think how I care my data which I have on moblie devices. I change phone very often because as the additional duty I test new devices in my company as a normal user. But I forgot I suppose to be even much more careful with these phones than usual customer - they are new on the market and I can't be sure if they are totally safe.
ReplyDeleteThanks to you text I know I have to do my homework and check what I should do to protect my information especially I store data which refer not only to me but also my friends, family or company.
Thank you Kasia for the article - it's almost eye-opening! And I say almost not because it's not a good article - it's great! It's me who has their eyes closed for the security factors. I have a smartphone with Android system but I don't install to much apps, only ones coming from trusted sources so I feel that I don't need to b be worried. I might install myself an antivirus app but I never thought of it before - I actually don't do anything special to ensure safety of my phone. I work at a small company and we don't have too many policies, certainly no BYOD policy is in place. I also don't read about mobile security, so I don't know any interesting facts :( But I will definitely keep my eyes open for mobile security in the future - thank you for that!
ReplyDelete1. Do you protect your mobile data? How?
ReplyDeleteDo not store any risky data on my mobile phone :)
2. Do you have any policies regarding BYOD at work?
If so, are the policies difficult to follow?
Simple and clever - completly forbidden to use own devices at work, it can be sanctioned for employee in a very bad way.
If you want to work from home etc the only way is to use VPN which will help you managing your security.
3. Have you heard about any interesting facts from the mobile security area?
Yes, in was at the beginning of expansion on polish market. It is not about stolen data but still... about people being unaware of the fact that everything costs.
One guy from work brought a mobile with a less efficient mobile internet, which was still counting every kB sent/downloaded and paying for them. How big was his fury after receving the bill I can only imagine - I only suppose that his childrens had a hard time downloading apps/games which android, by default, updates quite frequently..
I keep only contact details and a photos in my phone. I also don’t download any application. So I wasn’t thinking about any protection. However, it is good to know about the dangers of its absence (that protection). Thanks to your article I will seriously think about it.
ReplyDeleteIn my work use the network on own devices is possible by connecting to the network for guests. Of course, after registering the device with network administrator and obtaining the password. Password for guest is generated for a particular device.
Regarding interesting facts from the mobile security area, I must admit, that is completely unfamiliar for me.
It' s a very interesting and practical article. Thanks a lot!
Great article! I think it cannot be repeated enough - check permissions before installing an app on Android!
ReplyDeleteI, for one, like how the Android ecosystem is set up. The huge amount of security threats is a function of how liberal Google is with what you can do on your phone. Some developers use it to create awesome apps, especially when you go rooted, and some use it for ill by adding malware to innocent looking apps.. It's very hard to permit the first without allowing to some extend the other. If you install apps from reputable sources you are actually quite safe. Huge majority of those infections comes from markets where app piracy is rampant and people are downloading .apk files from random places on the internet.
Also, there are ways of revoking permissions to already installed apps (a completely unlocked phone is required though) so you can use certaing apps without the entire world tracking your browsing habits.
Regarding the passwords I'm actually amazed how little people are using "password" and "1234". Only 4% of people used "1234" to lock their iphone. The most popular password was used by 15 thousand out of 2 million people. I would have guessed much more than that! Those numbers actually made me quite surprised how good people became with their passwords:)
Very good article, subject is very interesting and I had been reading about it for some time, here is one of more complete information about NSA methods and devices:
ReplyDeletehttp://leaksource.wordpress.com/2013/12/30/nsas-ant-division-catalog-of-exploits-for-nearly-every-major-software-hardware-firmware/
that stands for itself
Deletehttp://www.youtube.com/watch?v=b0w36GAyZIA#t=442